
Atiq Ahmed, a former lawmaker in India’s parliament, convicted of kidnapping, was shot dead along with his brother while police were escorting them for a medical check-up in a slaying caught on live television on Saturday. CNN’s Vedika Sud reports.
Source link
Category: Uncategorized
-

Repeated gunshots fired on live TV as ex-lawmaker shot by assassins
-

World’s longest purpose-built cycling tunnel opens in Norway
Editor’s Note: Sign up for Unlocking the World, CNN Travel’s weekly newsletter. Get news about destinations opening, inspiration for future adventures, plus the latest in aviation, food and drink, where to stay and other travel developments.
CNN
—
There are many ways to explore the seven mountains that surround the picturesque UNESCO World Heritage city of Bergen on Norway’s fjord-studded west coast. The newest, however, might well be record-breaking.
A three-kilometer-long (1.8-mile) cycling and pedestrian tunnel has been blasted through the base of Løvstakken mountain and its makers say it’s the longest purpose-built tunnel of its kind.
Fyllingsdalstunnelen, as it’s known, opened on April 15 with a family day of sporting activities, following four years of construction that began in February 2019. The state-funded mega-project cost close to $29 million, or 300 million Norwegian kroner.
“We Norwegians are usually modest people,” Camilla Einarsen Heggernes, a spokesperson for rail company Bybanen Utbygging, tells CNN, “But in this instance we would say that the tunnel is 100% state of the art.”

It takes a little under 10 minutes to whizz through the tunnel by bike and around 40 if strolling by foot. To break up the monotony of the windowless tunnel, there are a variety of art installations throughout, as well as different colors and lighting to help users place where they are on the journey and offer a sense of direction.
At the center point is a “sundial” installation – where the sun definitely will never shine – which shows the time of day, again helping to orientate visitors and also to break up the otherwise long line of sight. The tunnel is otherwise perfectly straight, apart from slight curvatures at entrance and exit.
If you’re wondering how cyclists and pedestrians can use the same space, there are two lanes in the tunnel: a 3.5-meter wide bike lane and a 2.5-meter-wide lane for walkers and runners. “We have laid down a blue rubber flooring throughout the tunnel, similar to an athletic track, explains Einarsen Heggernes. “This makes it more pleasant to use than if one would just walk on asphalt.”

The new tunnel came about as a byproduct of Bergen’s second Bybanen tram line, which opened in November 2022. The tram line through the mountain required a parallel evacuation tunnel, so the developers decided to make the new tunnel multipurpose.
Bergen is Norway’s second-largest city and the port city is linked to Oslo, the Norwegian capital, by the 496-kilometer Bergensbanen railway line. This stunning rail journey crosses Europe’s largest high mountain plateau, the Hardangervidda, and its snow-clad vistas were the backdrop for the battle scenes in the “Star Wars” sequel “The Empire Strikes Back.”
While the Fyllingsdalstunnelen is pitching itself as the world’s longest purpose-built cycle tunnel, the reason for that caveat is the 3.6-kilometer-long Snoqualmie Tunnel in Washington, just east of Seattle. This former train tunnel is now a passageway for cyclists, runners and walkers and is part of the 250-mile Palouse to Cascades State Park Trail.
Six European cities made it in CNN Travel’s recent roundup of 10 of the world’s most bike-friendly cities. Copenhagen has 385 kilometers of bike lanes, having introduced its first one way back in 1892. Strasbourg in France has around 6,000 bikes available at self-service stations 24/7 which tourists can use. And the Swiss capital of Bern has a exhilarating downhill trail for riders who feel the need for speed. The best bit is that cyclists can get a funicular up to the top then ride down – no uphill struggle.
-
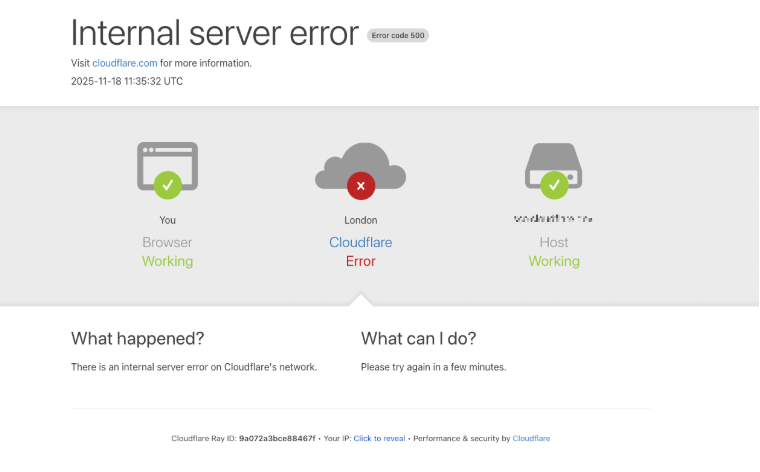
The Cloudflare Outage May Be a Security Roadmap – Krebs on Security
An intermittent outage at Cloudflare on Tuesday briefly knocked many of the Internet’s top destinations offline. Some affected Cloudflare customers were able to pivot away from the platform temporarily so that visitors could still access their websites. But security experts say doing so may have also triggered an impromptu network penetration test for organizations that have come to rely on Cloudflare to block many types of abusive and malicious traffic.
At around 6:30 EST/11:30 UTC on Nov. 18, Cloudflare’s status page acknowledged the company was experiencing “an internal service degradation.” After several hours of Cloudflare services coming back up and failing again, many websites behind Cloudflare found they could not migrate away from using the company’s services because the Cloudflare portal was unreachable and/or because they also were getting their domain name system (DNS) services from Cloudflare.
However, some customers did manage to pivot their domains away from Cloudflare during the outage. And many of those organizations probably need to take a closer look at their web application firewall (WAF) logs during that time, said Aaron Turner, a faculty member at IANS Research.
Turner said Cloudflare’s WAF does a good job filtering out malicious traffic that matches any one of the top ten types of application-layer attacks, including credential stuffing, cross-site scripting, SQL injection, bot attacks and API abuse. But he said this outage might be a good opportunity for Cloudflare customers to better understand how their own app and website defenses may be failing without Cloudflare’s help.
“Your developers could have been lazy in the past for SQL injection because Cloudflare stopped that stuff at the edge,” Turner said. “Maybe you didn’t have the best security QA [quality assurance] for certain things because Cloudflare was the control layer to compensate for that.”
Turner said one company he’s working with saw a huge increase in log volume and they are still trying to figure out what was “legit malicious” versus just noise.
“It looks like there was about an eight hour window when several high-profile sites decided to bypass Cloudflare for the sake of availability,” Turner said. “Many companies have essentially relied on Cloudflare for the OWASP Top Ten [web application vulnerabilities] and a whole range of bot blocking. How much badness could have happened in that window? Any organization that made that decision needs to look closely at any exposed infrastructure to see if they have someone persisting after they’ve switched back to Cloudflare protections.”
Turner said some cybercrime groups likely noticed when an online merchant they normally stalk stopped using Cloudflare’s services during the outage.
“Let’s say you were an attacker, trying to grind your way into a target, but you felt that Cloudflare was in the way in the past,” he said. “Then you see through DNS changes that the target has eliminated Cloudflare from their web stack due to the outage. You’re now going to launch a whole bunch of new attacks because the protective layer is no longer in place.”
Nicole Scott, senior product marketing manager at the McLean, Va. based Replica Cyber, called yesterday’s outage “a free tabletop exercise, whether you meant to run one or not.”
“That few-hour window was a live stress test of how your organization routes around its own control plane and shadow IT blossoms under the sunlamp of time pressure,” Scott said in a post on LinkedIn. “Yes, look at the traffic that hit you while protections were weakened. But also look hard at the behavior inside your org.”
Scott said organizations seeking security insights from the Cloudflare outage should ask themselves:
1. What was turned off or bypassed (WAF, bot protections, geo blocks), and for how long?
2. What emergency DNS or routing changes were made, and who approved them?
3. Did people shift work to personal devices, home Wi-Fi, or unsanctioned Software-as-a-Service providers to get around the outage?
4. Did anyone stand up new services, tunnels, or vendor accounts “just for now”?
5. Is there a plan to unwind those changes, or are they now permanent workarounds?
6. For the next incident, what’s the intentional fallback plan, instead of decentralized improvisation?In a postmortem published Tuesday evening, Cloudflare said the disruption was not caused, directly or indirectly, by a cyberattack or malicious activity of any kind.
“Instead, it was triggered by a change to one of our database systems’ permissions which caused the database to output multiple entries into a ‘feature file’ used by our Bot Management system,” Cloudflare CEO Matthew Prince wrote. “That feature file, in turn, doubled in size. The larger-than-expected feature file was then propagated to all the machines that make up our network.”
Cloudflare estimates that roughly 20 percent of websites use its services, and with much of the modern web relying heavily on a handful of other cloud providers including AWS and Azure, even a brief outage at one of these platforms can create a single point of failure for many organizations.
Martin Greenfield, CEO at the IT consultancy Quod Orbis, said Tuesday’s outage was another reminder that many organizations may be putting too many of their eggs in one basket.
“There are several practical and overdue fixes,” Greenfield advised. “Split your estate. Spread WAF and DDoS protection across multiple zones. Use multi-vendor DNS. Segment applications so a single provider outage doesn’t cascade. And continuously monitor controls to detect single-vendor dependency.”